昨晚要發表文章又發現似乎怪怪的,不曉得是不是修正過的後遺症><”
只要是發表一篇有關 phpMyVisites 的文章。關於訪客計數的,總是會有怪怪的問題出現。
一開始是為了貼上phpMyVisites 寄給我的信件內容
You are receiving this email from phpMyVisites (php web analytics) because
you have downloaded the product, registered for the newsletter or
participated in the forums.
The phpMyVisites team announces the immediate availability of phpMyVisites
2.4 which addresses a *critical* security issue in versions greater than
2.3b3. There are automatic attacks running on Russian servers that are
infecting phpMyVisites installations. When infected, aaphp shellis installed
on the server which can give total server control to the attacker.
All phpMyVisites users are *urged* to update their existing phpMyVisites to
the 2.4 release. Please find more information about the issue on the official
website: http://www.phpmyvisites.us
We will not be releasing any further phpMyVisites versions after 2.4. The
team has been working over the last two years on a new and improved project,
Piwik, which aims to be an open source alternative to Google Analytics.
Piwik is evolving rapidly and now has more than 30,000 users in more than 33
languages! New features are added every month. We recommend that you start
using Piwik as a replacement for phpMyVisites for your web analytics.
* phpMyVisites 2.4 downloads http://www.phpmyvisites.us/downloads.html
* Piwik http://piwik.org
* Piwik online demo http://piwik.org/demo
PS:結果就不小心剛好出現了dreamhost的阻檔關鍵字,讓整個blog掛掉。初看還以為是前幾天網頁被修改後,修正回來的後遺症。但後來發現不是這樣的。因為這樣,我的blog重新安裝了最少三四次,還重新確認檔案的時間,就什麼都沒發現。
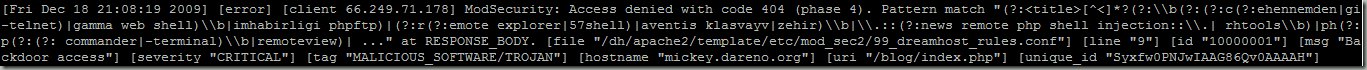
以下是的log資料
[Fri Dec 18 21:54:50 2009] [error] [client 119.77.xxx.xxx] ModSecurity: Access denied with code 404 (phase 4). Pattern match
"(?:<title>[^<]*?(?:\\b(?:(?:c(?:ehennemden|gi-telnet)|gamma web shell)\\b|imhabirligi phpftp)|(?:r(?:emote explorer|57shell)|aventis klasvayv|zehir)\\b|\\.::(?:news remote aphp shell injection::\\.| rhtools\\b)|ph(?:p(?:(?: commander|-terminal)\\b|remoteview)| …"at RESPONSE_BODY. [file"/dh/apache2/template/etc/mod_sec2/99_dreamhost_rules.conf"] [line "9"][id "10000001"] [msg "Backdoor access"] [severity "CRITICAL"] [tag "MALICIOUS_SOFTWARE/TROJAN"] [hostname "hostname"] [uri "/blog/wp-admin/post.php"] [unique_id "SyxqqUPNJwIAAHZQwccAAAAF"]
再來在log裡看到
[Wed Dec 16 17:34:38 2009] [error] [client 119.77.133.161] Request exceeded the limit of 10 internal redirects due to probable configuration error. Use ‘LimitInternalRecursion’ to increase the limit if necessary. Use ‘LogLevel debug’ to get a backtrace.
看一下上面的log資料又不知道是跟哪些東西有關了><”
之後cat了 99_dreamhost_rules.conf
又稍微看了一下一篇文章關於該檔案於別人的blog的介紹
Why DreamHost is awesome
They discovered and deleted the back door when I asked them to determine the source of the hack. Of course, this should have happened automatically, but it required them to notice this error log, which probably happens far too often:[Wed Nov 04 23:21:37 2009] [error] [client 213.163.xx.xx] ModSecurity: Access denied with code 404 (phase 4). Pattern match at RESPONSE_BODY. [file "/dh/apache2/template/etc/mod_sec2/99_dreamhost_rules.conf"] [line "9"] [id "10000001"] [msg "Backdoor access"] [severity "CRITICAL"] [tag "MALICIOUS_SOFTWARE/TROJAN"] [hostname "shii.org"] [uri "/tech/eula.php"] [unique_id "SvJ87EWjqwYAAB0XDO0AAAAX"]
For people who can’t read Apache logs: DreamHost is aware of this kind of exploit and put in a rule to prevent their box from getting rooted. The only fool affected by this hack was me.
Posted by Avery at 12:13 PM
via. http://angrysummerquietfall.blogspot.com/2009/11/how-i-was-hacked.html
花了一堆時間總算了解到底發生什麼事情,看起來是dreamhost對某些關鍵字有阻檔,所以在po文章的時候,無論是在phpBB下,或是Wordpress中,只要出現那其中的關鍵字的話,就會讓整個網站掛掉,花了一些時間試出來的,我想應該確定是這樣了,再加上看了 99_dreamhost_rules.conf 的 log 檔,更確信是這樣子了。
還好還以為整個blog又不行了。其實會發現這個的原因是在於,貼上別的內容都不會讓blog壞掉,可是貼上特定文章的內容確又有問題,雖然文章內容不多,但要想到是某些”關鍵字”造成的後過,若非有log檔可以比對確認,還真的是難以想到會有這樣的問題發生呢!?
Views: 0