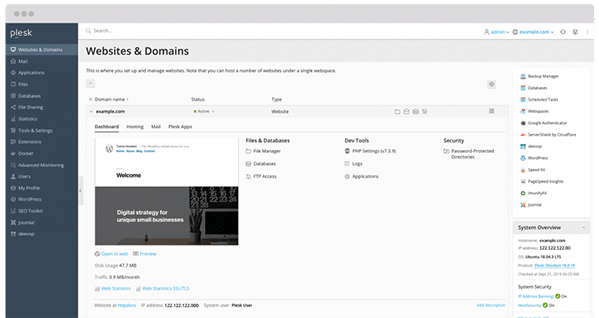
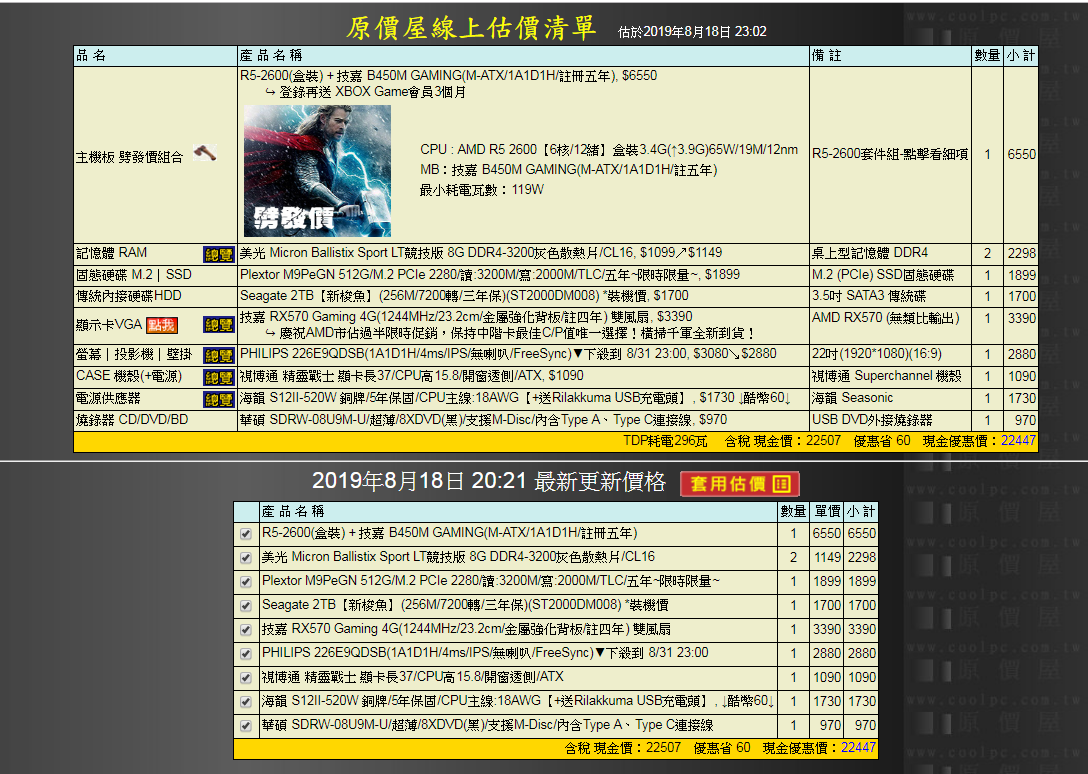
收到一封信
You are receiving this email from phpMyVisites (php web analytics) because
you have downloaded the product, registered for the newsletter or
participated in the forums.
The phpMyVisites team announces the immediate availability of phpMyVisites
2.4 which addresses a *critical* security issue in versions greater than
2.3b3. There are automatic attacks running on Russian servers that are
infecting phpMyVisites installations. When infected,aphp shellis installed
on the server which can give total server control to the attacker.
All phpMyVisites users are *urged* to update their existing phpMyVisites to
the 2.4 release. Please find more information about the issue on the official
website: http://www.phpmyvisites.us
We will not be releasing any further phpMyVisites versions after 2.4. The
team has been working over the last two years on a new and improved project,
Piwik, which aims to be an open source alternative to Google Analytics.
Piwik is evolving rapidly and now has more than 30,000 users in more than 33
languages! New features are added every month. We recommend that you start
using Piwik as a replacement for phpMyVisites for your web analytics.
* phpMyVisites 2.4 downloads http://www.phpmyvisites.us/downloads.html
* Piwik http://piwik.org
* Piwik online demo http://piwik.org/demo
看起來是說要更新,所以就點去官網看了一下。然後就看到下面的內容
phpMyVisites version 2.4: Security release
16 december 2009 – 17:00
We are releasing phpMyVisites 2.4 to address a security issue that was recently reported. The security issue is in the third party Clickheat library. We release phpMyVisites 2.4 without the Clickheat plugin. We urge every phpMyVisites user to update as soon as possible to phpMyVisites 2.4 as the security issue is critical.
Is your web server contaminated?
It can be hard to tell as the crackers are using quite clever techniques.
| If you have a file phpmv2/datas/thumbs.php, you are affected. |
結果在資料夾裡還真的找到了這個玩意兒,檔案內容開頭是用<?php eval(gzinflate(base64_decode( 接著後面是一堆亂碼,需要解開大概又要寫支轉碼程式了吧><”,但我想上網找會比較快,只是要知道被感染的路徑是在哪,這樣才好找出問題所在。
- If you are on a dedicated server, try to execute
ps fauxand look for SSH connections that are not supposed to be there (eg.sshd fakelogin@privfakelogin being a login that doesn’t exist on your server or is not supposed to exist). - Look in your website directories, are there new files, especially suspicious looking files like numbers 8475875.php or styles.css.php or fotter.php?
- Are there new .htaccess that are not supposed to exist?
- look at your actual website files (especially if written in php), do they contain code that is not yours at the top or at the bottom? Things like base64_decode, eval, gzinflate, are a sign that you are infected.
- Note: do not only look in phpmv2/ files, also look in your website files or any file on your server (to help, look at files that have a modification time that is suspicious)
We recommend that you rollback your servers to a clean backup and you re-install the new version of phpMyVisites 2.4, or update to Piwik.
Note: the development effort is now focused on Piwik, the new version of the most famous web analytics open source software! Visit piwik.org for more information about the open source alternative to Google Analytics.
話說回來,PIWIK 看起來真的是漂亮許多了。
下次再來裝吧。
- 會特別寫到這篇其實是因為前幾天就深受其害了, PHP的檔案被插入不明的程式碼,若非blog的後台不正常,然後又看到一些怪異的現像,不然還真不會發現已經被hack了。把內容修改回來又是另一篇故事了XD
這是被殖入的檔案(!?)..
Views: 0
![piwik-e280ba-web-analytics-reports7[1] piwik-e280ba-web-analytics-reports7[1]](https://blog.connie-brian.com/wp-content/uploads/sites/5/2009/12/piwike280bawebanalyticsreports71_thumb.png)
![ur6f9c[1] ur6f9c[1]](https://blog.connie-brian.com/wp-content/uploads/sites/5/2009/12/ur6f9c1_thumb.png)